About
The Auth module manages user logins for the video portal. By default, it uses Kaltura Authentication. Please note:
- To switch to SAML authentication, check out the SAML module.
- For multiple authentication methods, use the 'enableMultiAuth' setting.
- To help users change their login method after selecting 'Remember My Selection', they can visit: https://<partnerId>.mediaspace.kaltura.com/user/clear-login-selection or clear their browser cookies.
Authbroker
AuthBroker is a "gateway" that sits on the partner (account) level and manages authentication to Kaltura via external Identity providers (IdP). AuthBroker works with the Security Assertion Markup Language (SAML) and Open Authorization (OAuth 2.0) protocols. AuthBroker users are "shared users" (users who are shared between applications / instances in the partner).
AuthBroker works with a higher version of SAML and you no longer need to set up a new profile for each new account. You can set up profile(s) just once and easily use them in multiple applications/instances.
Configure
1. Go to your Configuration Management console, and navigate to the Auth module. You can also navigate directly: https://{your_video_portal_URL}/admin/config/tab/auth.
The Auth page displays.

2. In the Auth module window, configure the following:
demoMode - Set to 'Yes' if you want to enable the demo login mode. After entering any user or password combination, the user has an admin role.
showLogin - Set to 'Yes' if you want to show login / logout menu on site header.
phUser - user ID alternate field placeholder
phPwd - password alternate field placeholder
phLoginInstruction - login instructions
failedLoginEmailTemplate - Choose an email template from the menu to send when someone enters an email address that doesn’t match any existing user during login. Leave this field empty to disable the email. Note that email tokens are not supported in this template. You can configure templates in the emailtemplates module.
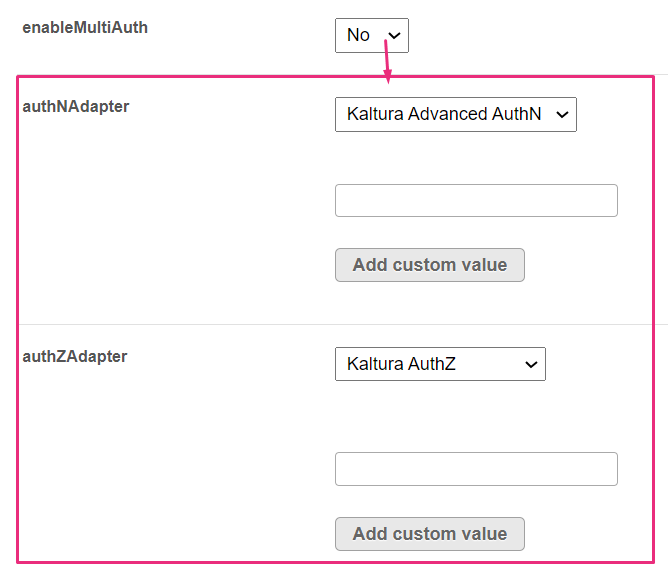
enableMultiAuth
enableMultiAuth set to 'No'
enableMultiAuth - Enable Multi-Authentication Methods configuration. If you leave the setting on 'No', complete the authNAdapter and authZAdapter fields below. If you select 'Yes', skip to the next section.
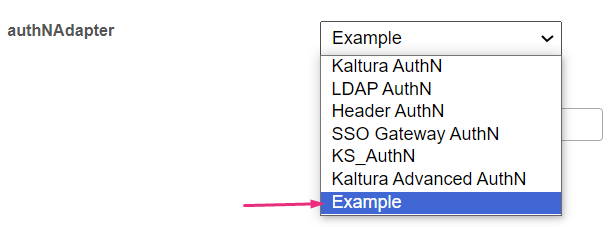
authNAdapter - What is the name of the PHP class for handling authentication? KalturaAuth enables the built-in User Management system (located at /admin/users).
When Theming is enabled, authNAdapter should be set to Kaltura Advanced AuthN.
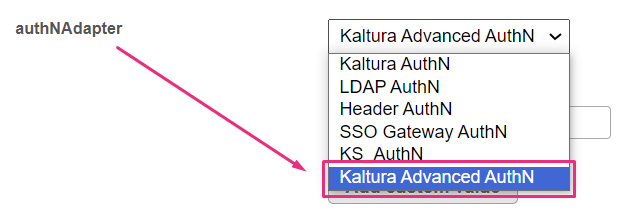
LdapAuth lets you use your organizational LDAP/AD server to authenticate users. To use your own custom class, enter the custom class name, then click 'Add custom value'.
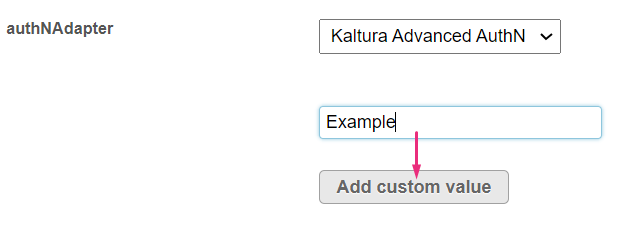
The value is added to the menu.
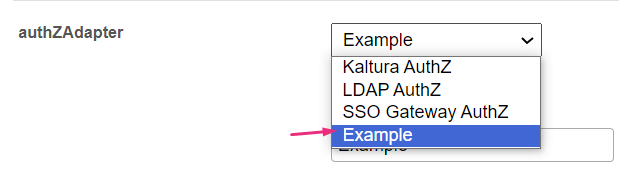
authZAdapter - What is the name of the PHP class for handling authorization? Authorization determines the user's role. KalturaAuth enables the built-in User Management system (located at /admin/users). LdapAuth lets you use your organizational LDAP/AD server to determine roles.
To use your own custom class, enter the custom class name, then click 'Add custom value'.
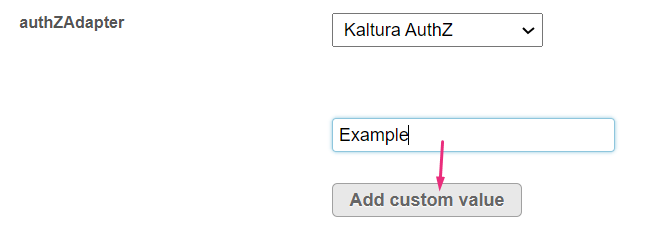
The value is added to the menu.
enableMultiAuth set to 'Yes'
enableMultiAuth - If you select 'Yes', a new section displays with multiAuthWelcome and multiAuthselect' fields, and a section for each authentication method you choose to configure.
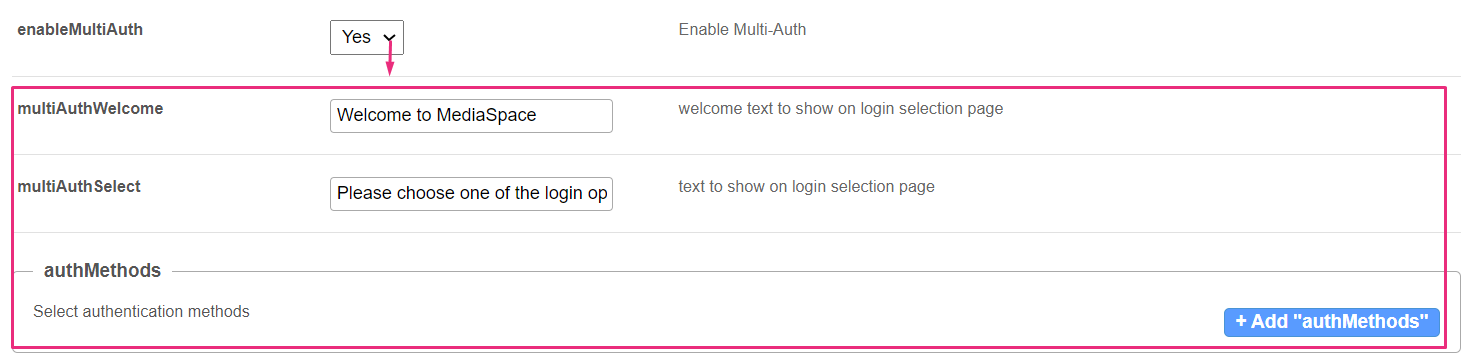
multiAuthWelcome - Enter welcome text to show on login selection page.
multiAuthSelect - Enter the text to show on login selection page.
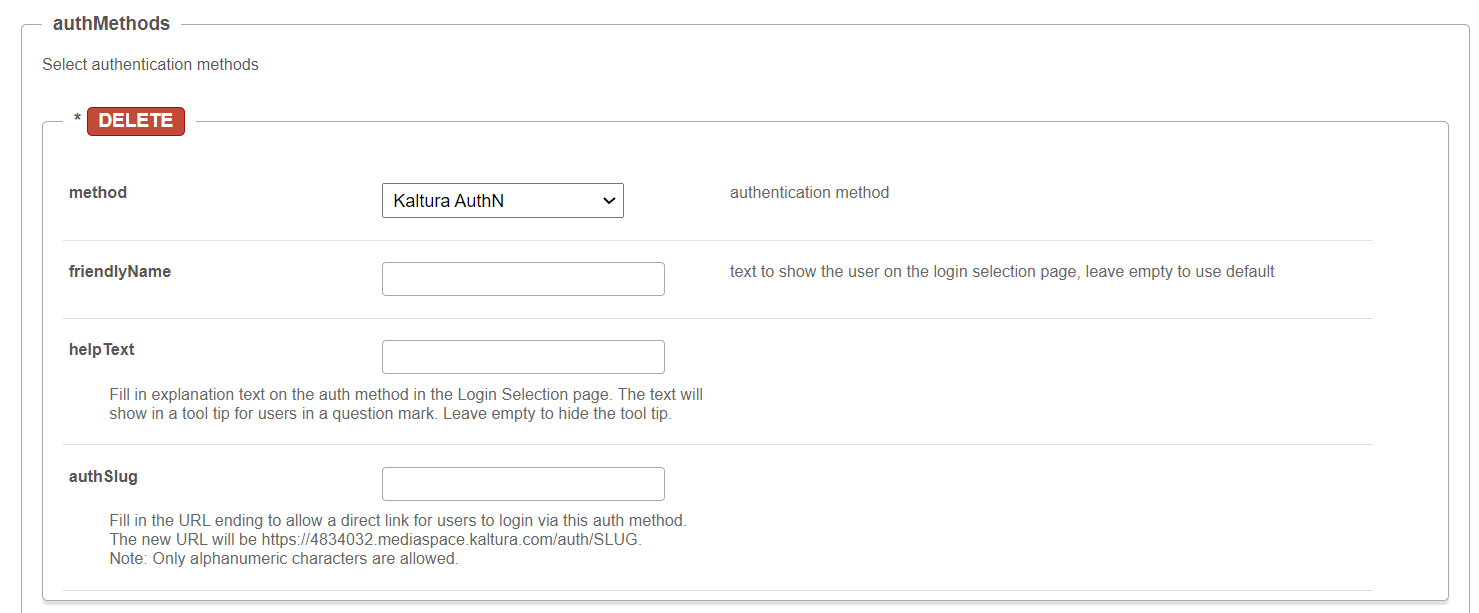
authMethods
Click +Add "authMethods".
A new section displays.
method - Choose an authentication method from the drop-down menu. friendlyName - Enter the text to show the user on the login selection page, leave empty to use default. helpText - Enter the text to show when hovering over the question mark on the login selection page, leave empty to use default. authSlug - Fill in the URL ending to allow a direct link for users to login via this auth method. The new URL will be https://<my_mediaspace_instance>.kaltura.com/auth/SLUG. Only alphanumeric characters are allowed. |
allowAnonymous - Can users access the Video Portal without logging in? If you select 'yes,' anonymousRole users can browse the galleries and view videos. For anonymousRole users, links/buttons for actions that require more advanced roles are displayed. When an anonymousRole user clicks a link/button that requires a more advanced role, a login screen is displayed.
anonymousGreeting - What text should be used in the header instead of an actual user name?
sessionLifetime - Set how long (in seconds) a MediaSpace user session can last. If set value is lower than the minimum of 3600 seconds (1h), the minimum wil be utilized.
refreshDetailsOnLogin - Select 'Yes' to update the user's details on Kaltura upon login (recommended).
refreshRoleOnLogin - Select 'Yes' to update the user's role on Kaltura upon login. Select 'No' to allow Video Portal admin to override the user's role through Kaltura user management.
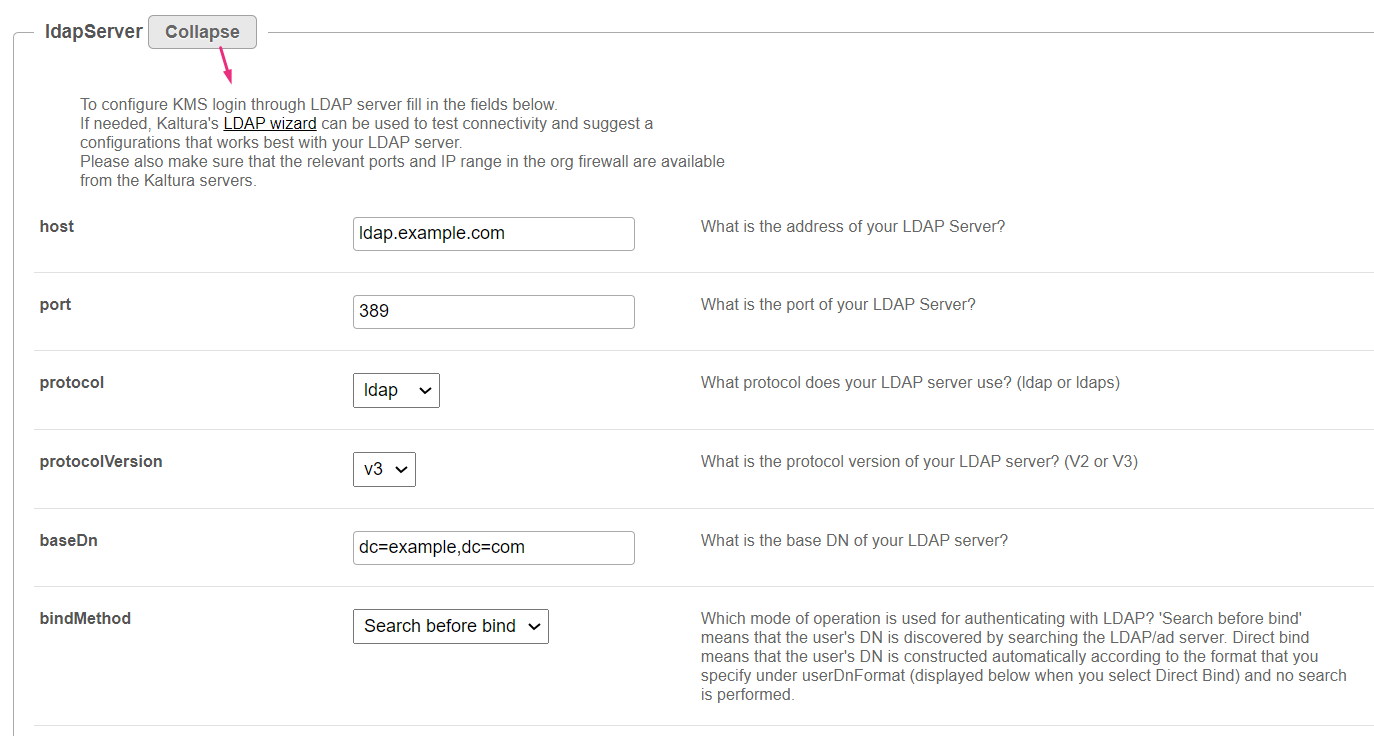
LdapServer
Click Expand to display the LDAP server options.
To configure Video Portal login through LDAP server, fill in the fields below. If needed, Kaltura's LDAP wizard can be used to test connectivity and suggest a configurations that works best with your LDAP server. Please also make sure that the relevant ports and IP range in the org firewall are available from the Kaltura servers. host - Enter the address of your LDAP Server. port - Enter the port of your LDAP Server. protocol - Enter the protocol your LDAP server uses (ldap or ldaps). Protocolversion - Enter the protocol version of your LDAP server (V2 or V3). baseDn - Enter the base DN of your LDAP server. bindMethod - Select the mode of operation used for authenticating with LDAP.
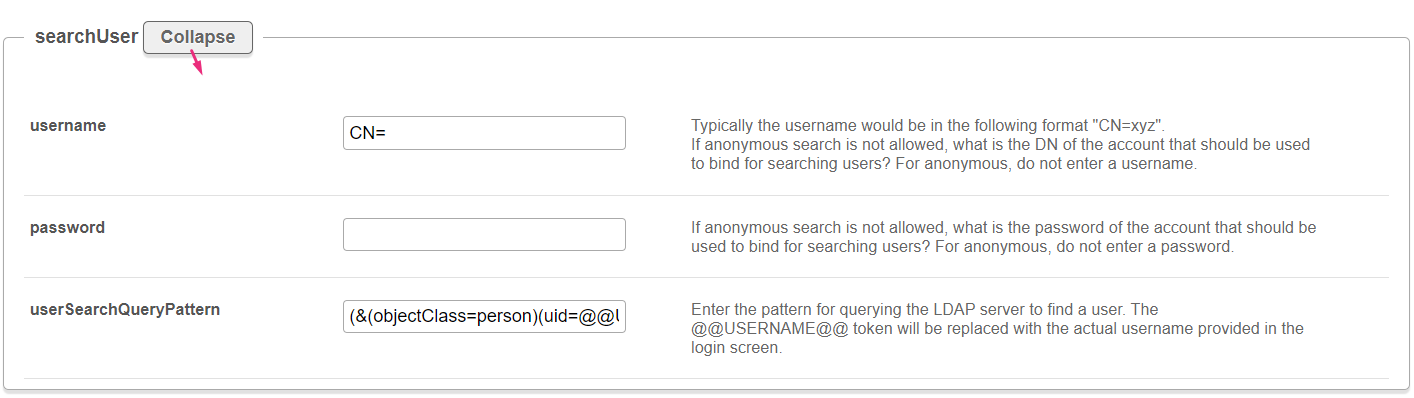
searchUserClick Expand to display the options.
username - Typically the username would be in the following format "CN=xyz". If anonymous search is not allowed, what is the DN of the account that should be used to bind for searching users? For anonymous, do not enter a username. password - If anonymous search is not allowed, what is the password of the account that should be used to bind for searching users? For anonymous, do not enter a password. userSearchQueryPattern - Enter the pattern for querying the LDAP server to find a user. The @@USERNAME@@ token will be replaced with the actual username provided in the login screen. emailAttribute - What is the name of the attribute on the user record that contains the user ID? If you do not want to sync email with Kaltura, do not enter an emailAttribute. firstNameAttribute - What is the name of the attribute on the user record that contains the user's first name? If you do not want to sync the first name with Kaltura, do not enter a firstNameAttribute. lastNameAttribute - What is the name of the attribute on the user record that contains the user's last name? If you do not want to sync the last name with Kaltura, do not enter a lastNameAttribute. tlsCipherSuite - Advanced: Control the value of LDAPTLS_CIPHER_SUITE environment variable. Use with extra care! |
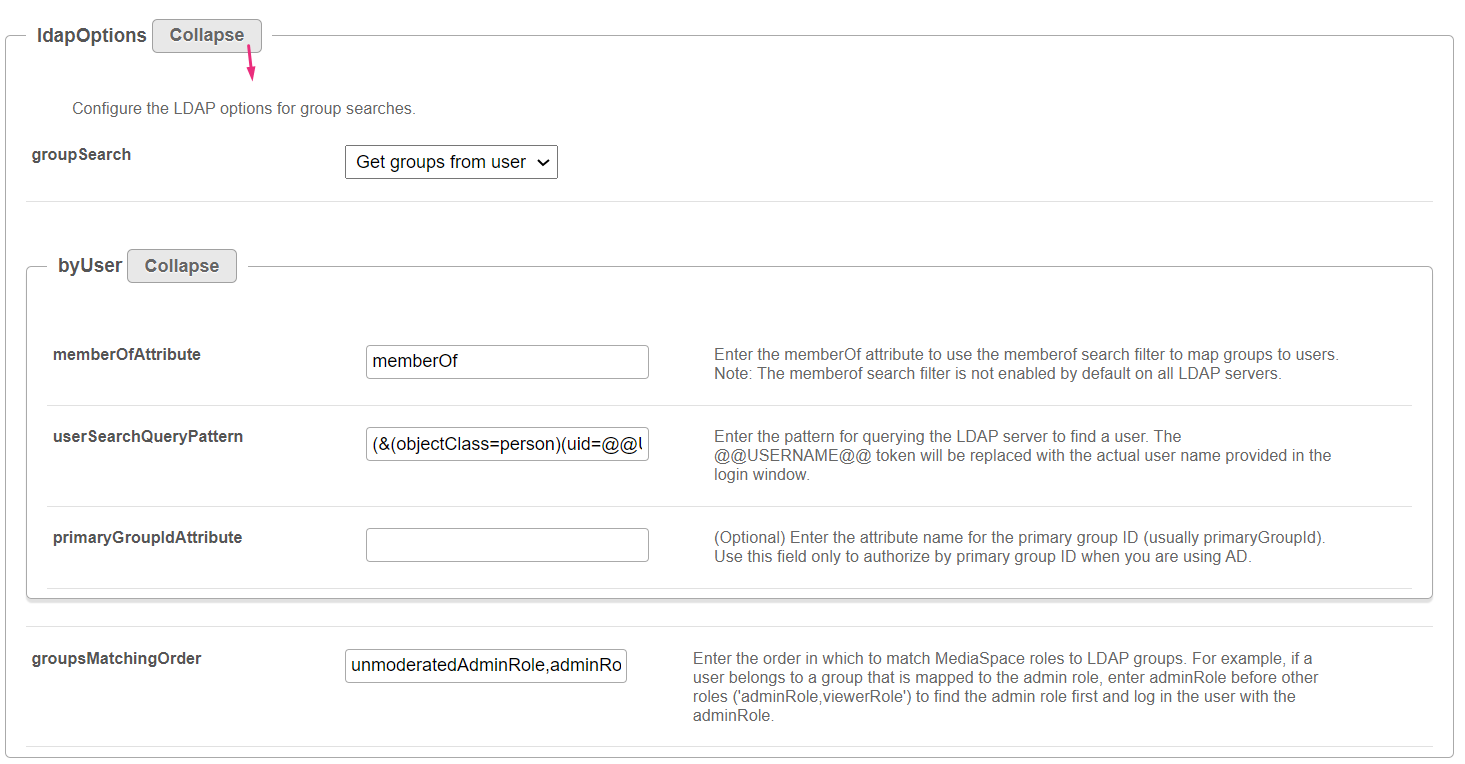
ldapOptions
Click Expand to display the LDAP Options for group searches.
Configure the LDAP options for group searches. groupSearch - Select the option from the drop-down menu: Get user from groups or Get groups from user
Get user from groupsIf you select Get user from groups, complete the byGroup section that follows:
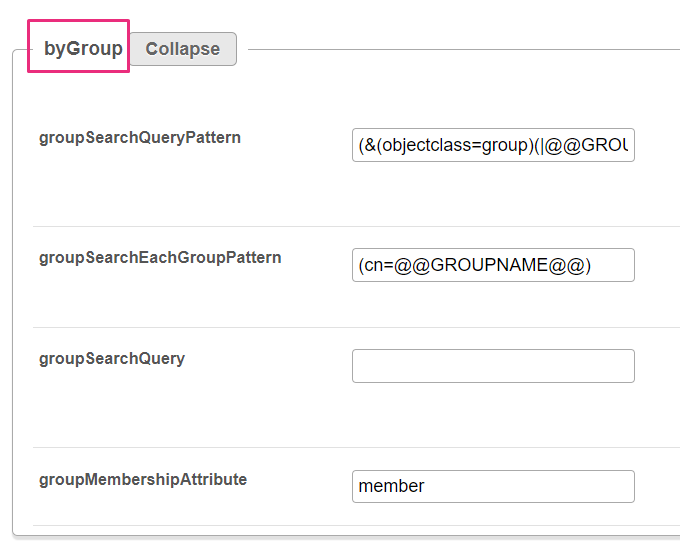
groupSearchQueryPattern - Enter the pattern for querying all groups in one query. The @@GROUPS_REPLACEMENTS@@ token will be replaced with the pattern that you specify under groupSearchEachGroupPattern (displayed below). The query results list all groups defined in the mapping settings. groupSearchEachGroupPattern - Enter the pattern for each group in the groupSearchQueryPattern (displayed above). This pattern is used multiple times: one time for each group defined in the mapping settings. The relation between the groups is OR. groupSearchQuery - Enter the LDAP query that finds all groups. This query runs only one time, so it returns all groups defined in the matching settings. If you enter a value for this LDAP query, the two settings displayed above (groupSearchQueryPattern and groupSearchEachGroupPattern) are not used. groupMembershipAttribute - Enter the attribute on a group record that lists the users who are members in the group. Get groups from userIf you select Get groups from user, complete the byUser section that follows:
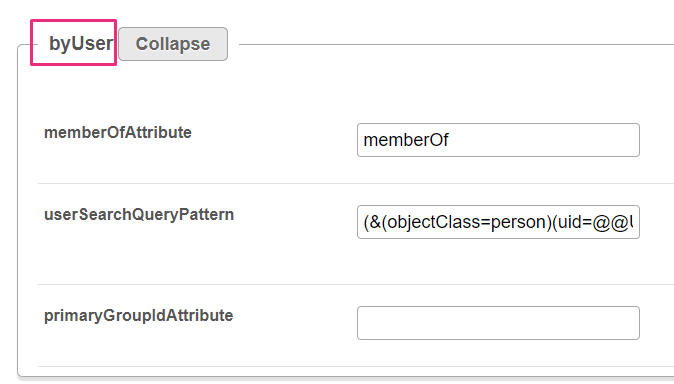
memberOfAttribute - Enter the memberOf attribute to use the memberof search filter to map groups to users. Note: The memberof search filter is not enabled by default on all LDAP servers. userSearchQueryPattern - Enter the pattern for querying the LDAP server to find a user. The @@USERNAME@@ token will be replaced with the actual user name provided in the login window. primaryGroupIdAttribute - (Optional) Enter the attribute name for the primary group ID (usually primaryGroupId). Use this field only to authorize by primary group ID when you are using AD. groupsMatchingOrder - Enter the order in which to match MediaSpace roles to LDAP groups. For example, if a user belongs to a group that is mapped to the admin role, enter adminRole before other roles ('adminRole,viewerRole') to find the admin role first and log in the user with the adminRole. |
ldapGroups
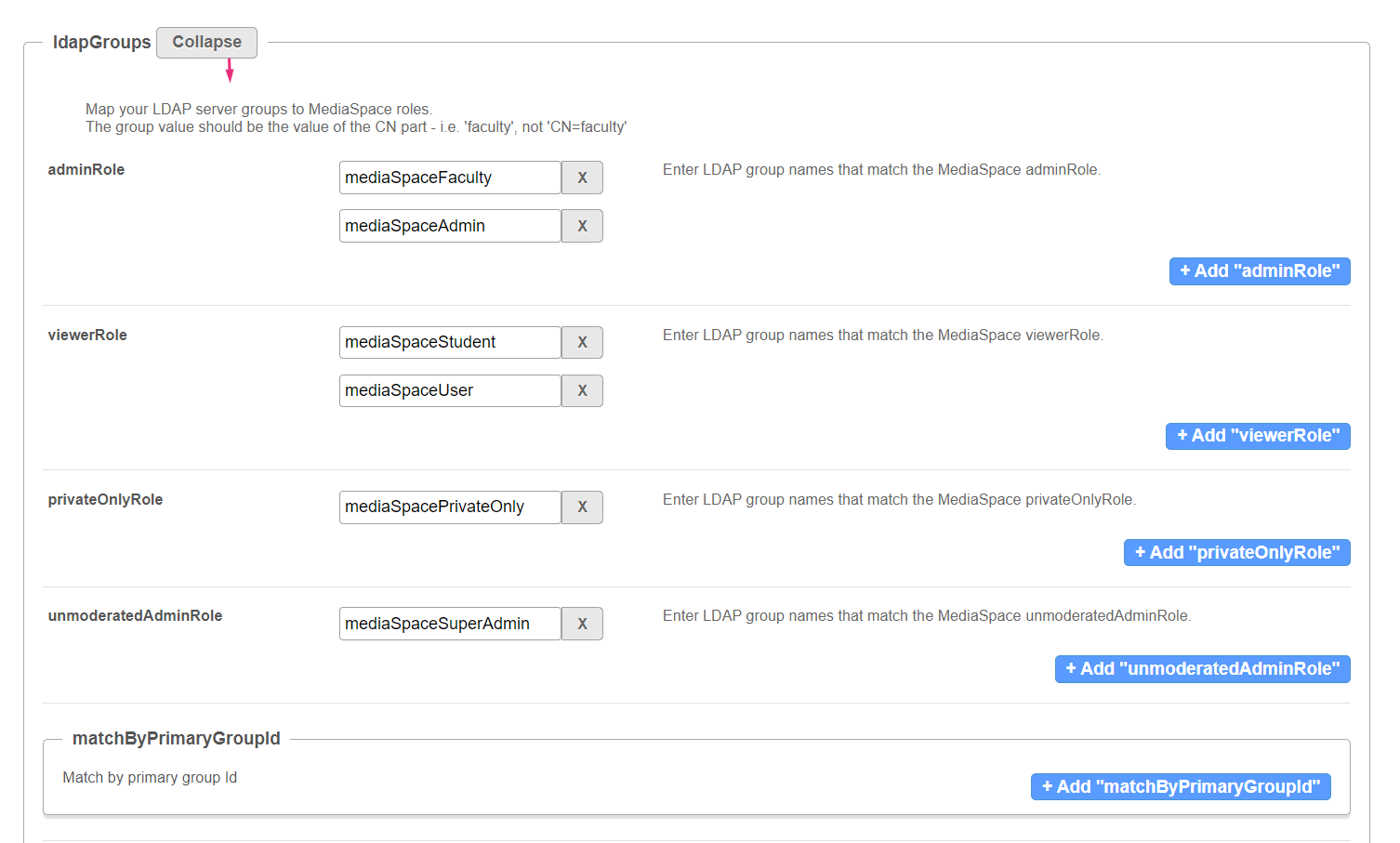
Click Expand to map your LDAP server groups to MediaSpace roles. The group value should be the value of the CN part - i.e. 'faculty', not 'CN=faculty'
adminRole - Enter LDAP group names that match the MediaSpace adminRole. Click +Add "adminRole" to add another role. viewerRole - Enter LDAP group names that match the MediaSpace viewerRole. Click +Add "viewerRole" to add another role. privateOnlyRole - Enter LDAP group names that match the MediaSpace privateOnlyRole. Click +Add "privateOnlyRole" to add another role. unmoderatedAdminRole - Enter LDAP group names that match the MediaSpace unmoderatedAdminRole. Click +Add "unmoderatedAdminRole" to add another role. matchByPrimaryGroupIdTo match by primary group ID, click +Add "matchByPrimaryGroupId". A new section displays.
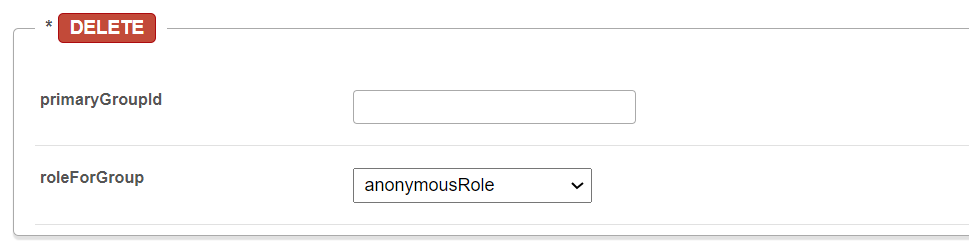
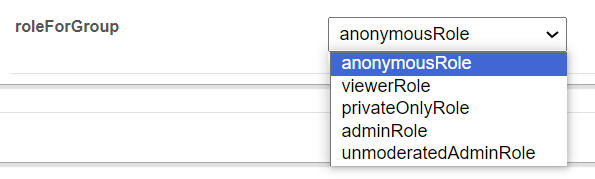
primaryGroupId - Enter ID. roleForGroup - Select the desired role from the drop-down menu.
|
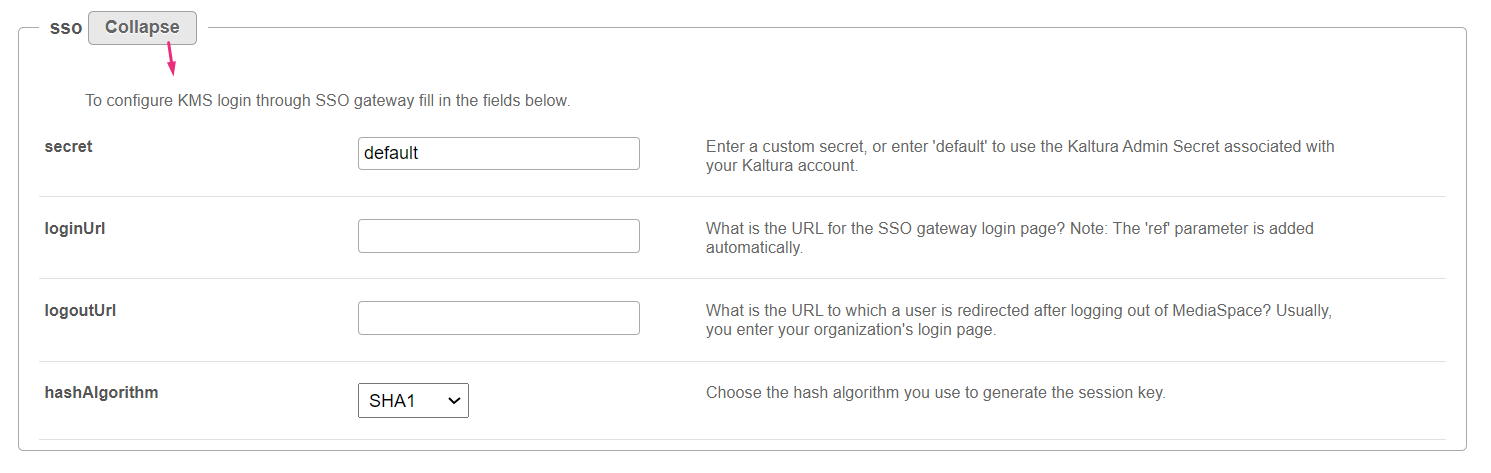
SSO
Click Expand to configure the Video Portal login through SSO gateway.
secret - Enter a custom secret, or enter 'default' to use the Kaltura Admin Secret associated with your Kaltura account. loginUrl - What is the URL for the SSO gateway login page? The 'ref' parameter is added automatically. logoutUrl - What is the URL to which a user is redirected after logging out of MediaSpace? Usually, you enter your organization's login page. hashAlgorithm - Choose the hash algorithm used to generate the session key - either 'SHA1' or 'SHA256'. |
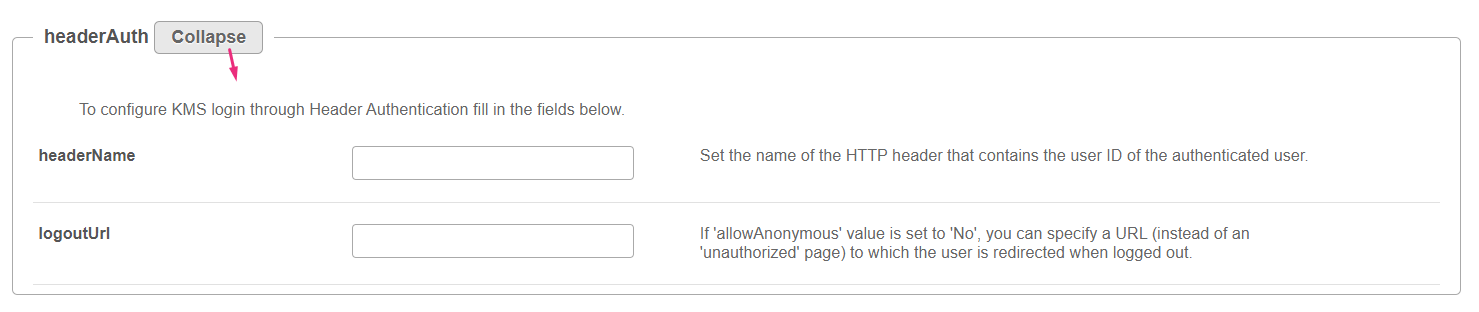
headerAuth
Click Expand to configure Video Portal login through Header Authentication.
headerName - Set the name of the HTTP header that contains the user ID of the authenticated user. logoutURL - If 'allowAnonymous' value is set to 'No', you can specify a URL (instead of an 'unauthorized' page) to which the user is redirected when logged out. |
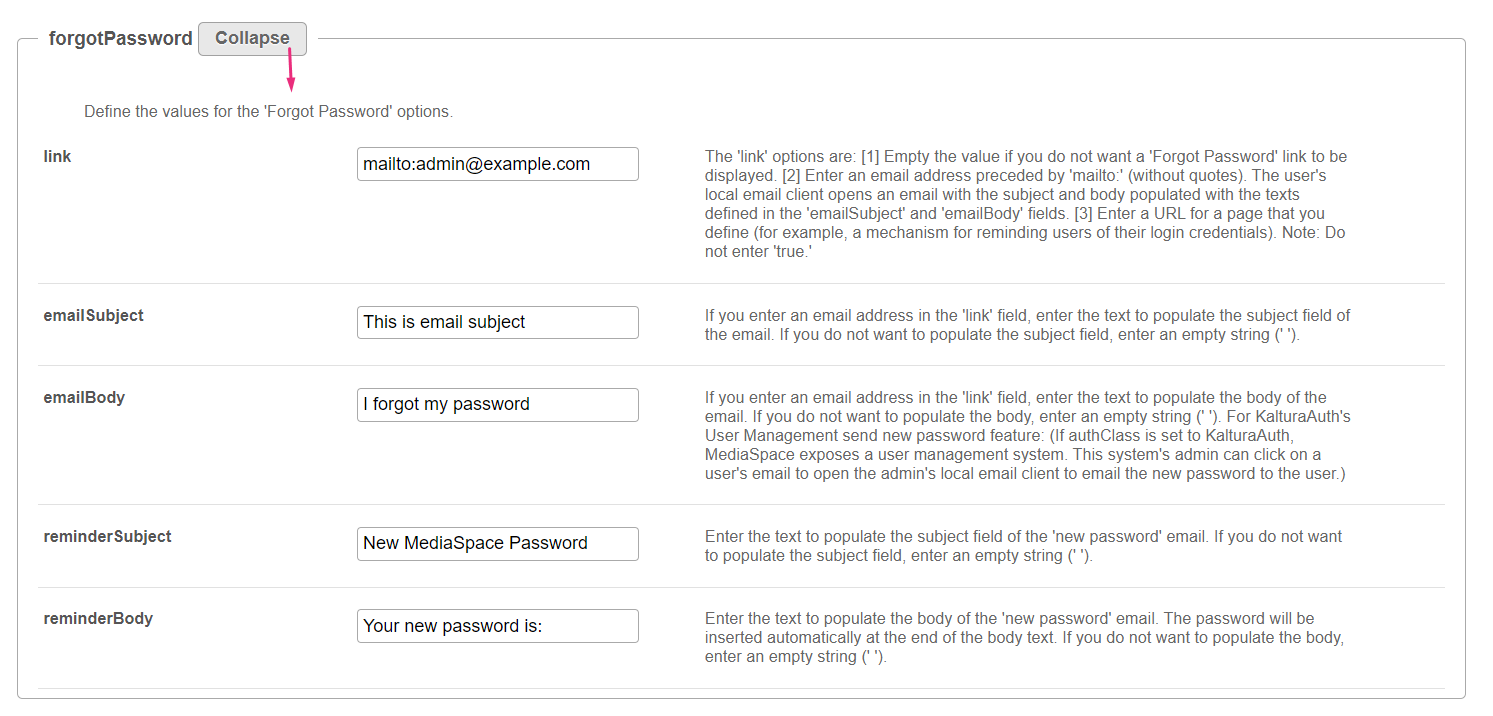
forgotPassword
Click Expand to define the values for the Forgot Password options.
link - The 'link' options are:
emailSubject - If you enter an email address in the 'link' field, enter the text to populate the subject field of the email. If you do not want to populate the subject field, enter an empty string (' '). emailBody - If you enter an email address in the 'link' field, enter the text to populate the body of the email. If you do not want to populate the body, enter an empty string (' '). For KalturaAuth's User Management send new password feature: (If authClass is set to KalturaAuth, MediaSpace exposes a user management system. This system's admin can click on a user's email to open the admin's local email client to email the new password to the user.) reminderSubject - Enter the text to populate the subject field of the 'new password' email. If you do not want to populate the subject field, enter an empty string (' '). reminderBody - Enter the text to populate the body of the 'new password' email. The password will be inserted automatically at the end of the body text. If you do not want to populate the body, enter an empty string (' '). |
adminsGroup - Enter a group ID to which any KMC or Events users will be added upon login to the site.
3. Click Save.